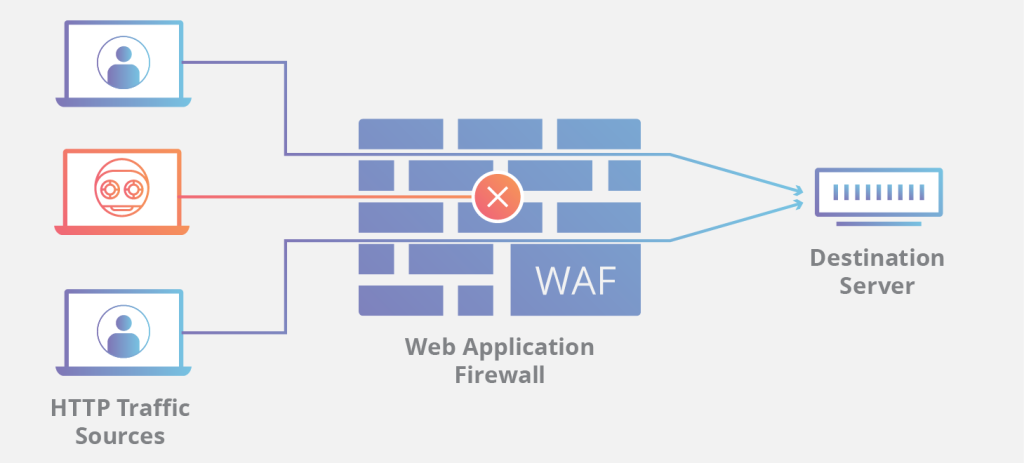
Hence, adopting a web application firewall (WAF) has become a necessity for organizations to prevent such threats. A WAF inspects and filters HTTP traffic on web applications, detecting and blocking malicious traffic without impacting genuine user requests.
What is a Web Application Firewall
A web application firewall (WAF) is a software- or hardware-level security system situated between the web application and the client. While a traditional firewall provides protection from threats at the network level, a WAF should be implemented to address application-level security threats. It examines the network traffic going in and out of your web applications for cyber threats. It stops various kinds of web application attacks like SQL injection, cross-site scripting (XSS), and other common threats.
A web application firewall benefits organizations by protecting their digital infrastructure in real time and adapting to new hacking techniques as they arise. There are many more reasons to amplify WAF deployment for today’s modern enterprises:
Why Organizations Need a Web Application Firewall More Than Ever
Rising Threat Scenario
Web applications are increasingly being targeted by cybercriminals using quickly evolving automated attack tools. A single vulnerability may result in severe damage. Attackers are now using botnets to conduct attacks, scanning thousands of websites for vulnerabilities in minutes. A WAF can counteract these automated attacks by blocking rogue traffic and stopping bad bots before they can cause damage to the web app.
Regulatory Mandates
Highly regulated organizations, such as financial institutions or healthcare providers, must maintain a high level of application security to comply with governmental regulations (PCI DSS for payment processing, for instance). Implementing a WAF is a significant component of policy enforcement, as it protects sensitive data such as credit card numbers, personally identifiable information (PII), healthcare records, and more.
Brand Protection
The cost of a data breach can be more damaging to a brand than regulatory fines. Organizations want to safeguard their goodwill, as it takes time to regain customer confidence. Branding impacts and data breach costs should always be taken into consideration.
Business Continuity
A DDoS attack, in particular, poses a significant threat to the availability of the web application. If the web app is not accessible, organizations cannot generate income. In cases where a business is completely dependent on its applications, operations may be forced to shut down temporarily until services are restored.
Key Web Application Firewall Features
- Customizable Rulesets: Since every application is different, being able to configure rules is essential to prevent false positives and stop as many attacks as possible.
- Real-Time Monitoring: The ability to watch traffic continuously and block threats as they occur.
- Scalability: A good WAF should be able to grow with the amount of traffic your application receives without compromising performance.
- Reporting and Analytics: Insights into incoming traffic and emerging threats to fine-tune your security policies.
Deployment Choices
- Cloud-Based WAF: Provided by third-party vendors, these can be deployed quickly without the need to purchase physical hardware.
- On-Premises Appliance: A physical security appliance deployed and maintained in your organization’s data center.
- Integrated Software: Software built into the application stack, ideal for environments requiring a high degree of customization.
The right choice depends on your organization’s size, budget, compliance needs, and the skills of your security team.
How to Securely Implement a WAF
- Inspect Traffic Flow: Understand how the application interacts with its libraries.
- Use in Conjunction with Other Security Solutions: A WAF is only one piece of a good security posture. Use intrusion prevention systems, secure coding practices, and vulnerability scanning.
- Maintain a Current Ruleset: Update rules frequently to address emerging threats.
- Log and Review Requests: Analyze logs to refine the ruleset and improve accuracy.
The Bottom Line
In the world of web applications, WAF solutions are critical. Where web applications are the lifeblood of business, a WAF can no longer be an afterthought — it is a necessity. WAFs serve as virtual sentries, allowing legitimate data to pass through while deflecting malicious payloads. By deploying a properly configured WAF, along with regular maintenance and updates, the likelihood of a security breach will dramatically decrease. Most importantly, customers will continue to trust the applications they rely on.





















